Table of Contents
- FREE 3+ Security Impact Analysis Templates in PDF
- 1. Security Impact Analysis Template
- 2. Security Impact Analysis Example
- 3. Food Security Impact Analysis Template
- 6 Steps to create the Security Impact Analysis
- FAQ’s
- Why do you perform the security Impact Analysis?
- How do you perform the Security Impact Analysis?
- How do you asses the impact?
- What are the advantages of Security Impact Analysis?
FREE 3+ Security Impact Analysis Templates in PDF
The security Impact Analysis is conducted by the structure official to work out the extent to that changes to the knowledge system have affected the protection state of the system. the protection impact analysis includes for example; reviewing security plans to grasp security management needs and reviewing the system style documentation to grasp management implementation and the way specific changes may have an effect on the controls.
FREE 3+ Security Impact Analysis Templates in PDF
1. Security Impact Analysis Template
 wtamu.edu
wtamu.edu2. Security Impact Analysis Example
 semanticscholar.org
semanticscholar.org3. Food Security Impact Analysis Template
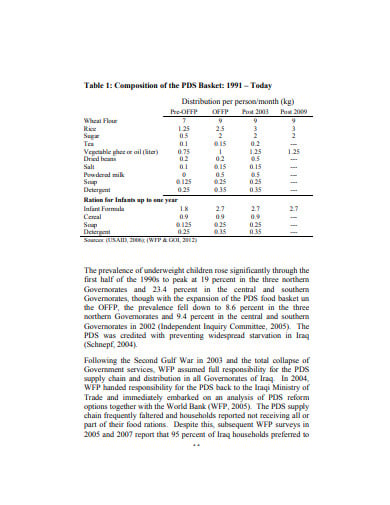 merit.unu.edu
merit.unu.edu6 Steps to create the Security Impact Analysis
The Security Impact Analysis is employed to gauge the planned impacts or the assumptions within the organization or its dynamical activity. The impact ways are used once comparison the various choices. it’s employed in the management or within the field of the strategic management. The risk analysis ways includes the techniques and therefore the management practices that helps to stop or control predictable risks. Here are the five Steps to form the protection impact analysis .
Step 1: Creating a core team
The creation of the tasks force of the professionals from within the organization that includes the owner, the IT head and managers of different teams or the functional areas, if necessary. The core team will lead the analysis, prepare the report and suggest the recommendations.
Step 2: Review the existing Security Policy
The organization may or might have the security policy in place already. If you don’t have one, now it’s the best time to review it to make sure it’s relevant to any recent market changes. Your security policy should cover the security strategies, data backup plans, password management policies, security update/patch timelines and other related details.
Step 3: Creating the database of IT assets
Prepare a comprehensive list of the software package and therefore the hardware assets that the organization owns. This includes the networks, servers, desktops, laptops, software package applications, websites, POS devices, the non-public devices that your employees use to visualize emails, external drives, etc.
Step 4: Understanding the Threats and Vulnerabilities
Prepare the listing of all the potential threats that the business might face supported past experiences, experiences of your peers, news reports, etc. establish the gaps within the system that these threats might presumably exploit. you’ll be able to use the IT security code that provides options like vulnerability scanning and alerts to spot the weak points within the applications and also the networks.
Step 5: Estimating the impact
Categorize the probability that every potential risk would happen as high, medium, or low. The chance level will increase if the likelihood is that high.
Step 6: Plan the controls
List the existing controls systems in place and outline further actions that can help mitigate the identified risks. These controls can include changes policies or procedures, applications, procurement, training, content, and configurations, or implementations of new applications and hardware.
FAQ’s
Why do you perform the security Impact Analysis?
The system requires changes in it. Whether those changes involve assessing objectives, allocating resources or drafting methods to reduce the expenses. And when someone makes a change request, it opens up the possibilities of the risks. The changes are reviewed by the right professionals often a change control board. then a security impact analysis is the next. It is that not everyone can conduct the analysis correctly. It requires an extensive amount of time to complete.
How do you perform the Security Impact Analysis?
The Security Impact Analysis can be utilized effectively by those with knowledge concerning the change should conduct the study. It is the best way to ensure details are not forgotten or inputted inaccurately. This is basically the tool to reduce the risks. The amount of the risks of the impact of the risks can make or break the system. Of course, if there are methods to reduce the chances of risks, a business must optimize the tools to do so. The analysis is one step in a process that will control fluctuations and changes.
How do you asses the impact?
The analysis takes a while to complete. It’s divided into different categories. It starts with the examination of the changes. The analysts must address this and its implications to the system or the processes. And how it might affect potential requests in the future. The Analysts investigate the hazards involved, the consequences of the risks, and the amount of the time and funds it will require to make the change the requests happen. Missing any information may affect the results.
What are the advantages of Security Impact Analysis?
The Security Impact Analysis works to prevent the surprises from popping up, surprises of risks aren’t welcome in any organization. If the data remains missing, the risks may end up greater than expected, thus harming the project and company immensely. It requires a lot of the hard work to complete, but being so thorough, Analysis helps to address risks concerns for any changes requests accurately. The result will provide those in charge of the necessary info to make informed decisions.






